With cyber threats becoming increasingly sophisticated and targeted, obsolete perimeter-based security architectures are not enough anymore. With the growing trend of remote work, cloud services, and hybrid IT infrastructures, organizations need more agile and responsive network security. This is where Fortinet ZTNA comes into play as a force to be reckoned with—upending how businesses manage access to applications and resources.
Fortinet Zero Trust Network Access provides a cutting-edge way of protecting users and devices by ensuring that there is no application, user, or device that is trusted in advance, even when they are inside the corporate network. Through this approach, organizations are able to reduce risk, minimize the attack surface, and enjoy end-to-end visibility in their digital ecosystems.
What Is Fortinet ZTNA?
Fortinet ZTNA, or Zero Trust Network Access, is a next-generation cybersecurity model that replaces legacy VPN-based access. Fortinet ZTNA offers secure and fine-grained access to applications based on real-time verification of user identity, device posture, and other contextual factors. In contrast to legacy models where trust is presumed within the network, Fortinet ZTNA is a never-trust, always-verified model.
Fortinet’s ZTNA is highly integrated in the Fortinet Security Fabric, allowing for effortless visibility and policy enforcement across users, endpoints, networks, and cloud. It provides access control to the application level, instead of network level access, and accommodates both on-premises and remote access users.
How Fortinet ZTNA Works
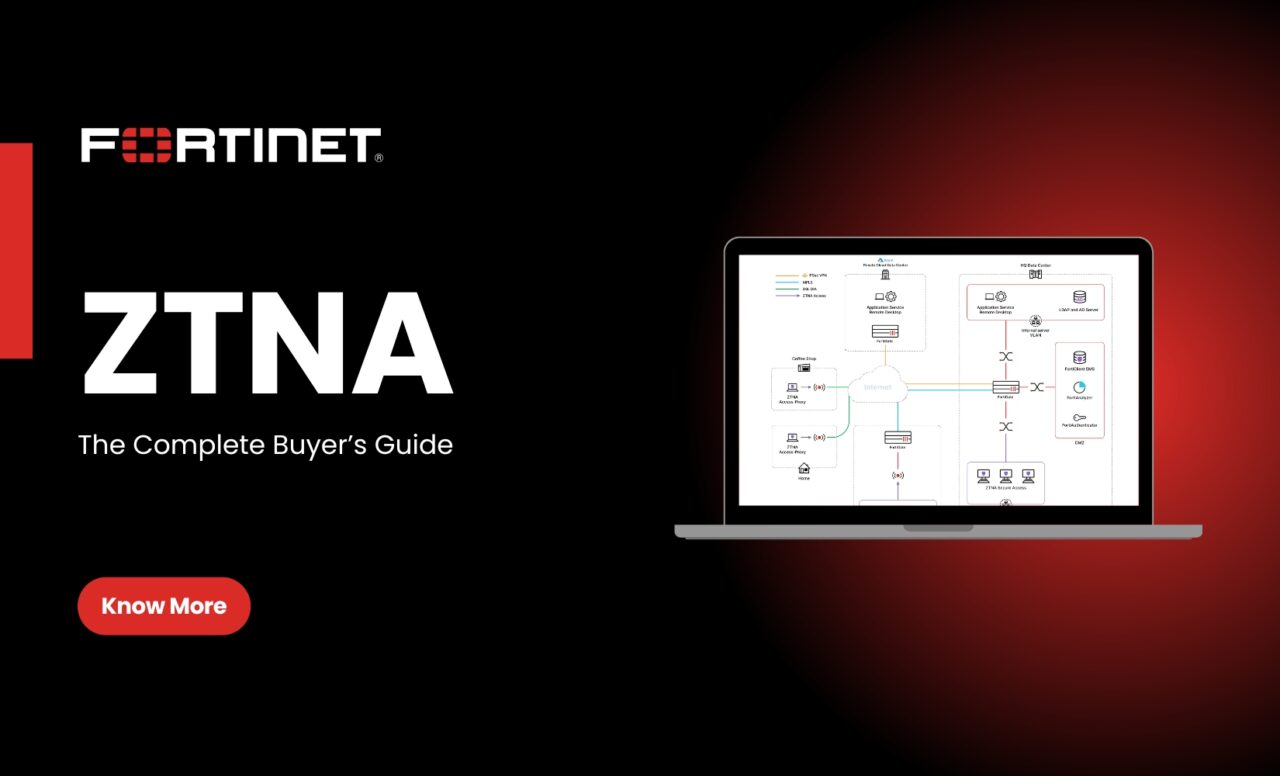
Fortinet ZTNA establishes a logical perimeter around every application and permits access only after ensuring the user and device satisfy security conditions in advance. This is possible by utilizing FortiClient, FortiGate next-generation firewalls, and FortiAuthenticator. After a user tries to access an application, Fortinet Zero Trust Network Access checks the request against identity, posture, and location policies prior to granting access. This control-aware significantly minimizes the chance of accessing an application without authorization and lateral movement in the network.
ZTNA policies in Fortinet are strictly associated with user groups and device profiles. This implies users obtain access to certain applications and resources they are legitimized for, and only if they are accessing from a compliant device. Fortinet Zero Trust Network Access also includes adaptive access, which dynamically adapts permissions on the basis of current alterations in user behavior or device health.
Benefits of Fortinet ZTNA
Fortinet ZTNA provides greater security and improved user experience than conventional remote access. To start with, it eliminates the notion of a trusted internal network, which makes breaches due to compromised user credentials much less likely. By dividing up access right down to the level of individual applications, Fortinet Zero Trust Network Access prevents attackers from moving laterally between systems even if they achieve initial access.
The solution also streamlines the IT environment by consolidating several remote access tools under a single, unified platform. Because Fortinet ZTNA runs natively on the Fortinet ecosystem, it eliminates complexity and operational overhead for security operations teams. With telemetry, logging, and analytics built-in, organizations can have full visibility into access patterns and identify anomalies in real time.
Another key benefit is scalability. Whether facilitating thousands of remote workers or granting access to cloud-native applications, Fortinet Zero Trust Network Access provides consistent performance and centralized control. It also includes automation and orchestration, allowing easy scaling of policies across dispersed environments.
Use Cases Across Industries
Fortinet ZTNA is deployable in nearly every industry. In healthcare, it keeps sensitive patient information safe by making sure only approved medical personnel can reach hospital applications from sanctioned devices. In finance, Fortinet Zero Trust Network Access assists in fulfilling compliance requirements by applying strict access rules to trading desks, databases, and customer portals. Education, it makes sure students and staff access materials securely, whether on-site or off-site.
Manufacturing companies use Fortinet ZTNA to actively secure access to their OT environments, which are frequent targets of industrial cyberattacks. Retail companies count on Zero Trust Network Access for protecting point-of-sale hardware, supply chain websites, and employee management portals, providing round-the-clock protection without sacrificing ease of use.
How to Get Fortinet ZTNA
Companies intending to implement Fortinet Zero Trust Network Access should first approach an authorized Fortinet partner. Who can take them through the deployment, integration, and optimization process. A trusted provider for this is Juara IT Solutions—a certified Fortinet partner and reseller with operations in India, UK, USA, Australia, and Malaysia.
Juara IT Solutions provides end-to-end solutions for the deployment of Fortinet ZTNA. Including solution evaluation, infrastructure preparedness, setup, training, and on-going support. Having extensive experience with the Fortinet technologies and hands-on implementation skills. They are a trusted partner for organizations of various sizes. Whether your requirement is to upgrade legacy VPNs or protect remote employee access. Juara IT Solutions can customize a ZTNA rollout that fits into your security plan and business goals.
In order to experience Fortinet ZTNA solutions. Book a consultation or ask for a demo, go to the official Fortinet Partner.
Final Thoughts
Fortinet ZTNA is a next-generation security solution that works to solve today’s most acute access control issues. Based on a Zero Trust philosophy. It allows organizations to minimize risk, avoid data breaches, and simplify access in hybrid environments. Fortinet Zero Trust Network Access is different from traditional VPNs, which offer wide and usually unnecessary access. It provides accurate, context-based permissions that safeguard users and essential assets.
As the digital landscape keeps changing, business organizations need to embrace wiser, more responsive security solutions. Fortinet ZTNA provides a safe, scalable, and streamlined method of dealing with user access in a decentralized world. Thanks to partners with expertise like Juara IT Solutions, organizations can install Zero Trust Network Access with assurance and speed.
FAQs
What is Fortinet Zero Trust Network Access?
Fortinet ZTNA is a Zero Trust Network Access solution. That authenticates users and devices prior to allowing them to access particular applications, eliminating the risk of unauthorized access.
In what ways does Fortinet ZTNA differ from traditional VPNs?
While VPNs offer network-wide access. Fortinet Zero Trust Network Access only offers access to designated applications based on user identity, device posture, and contextual factors.
Is Fortinet ZTNA applicable for use with remote and in-office employees?
Yes, Fortinet Zero Trust Network Access enables hybrid workforces. By securely controlling access for remote and on-premises users on varying devices.
Is Fortinet Zero Trust Network Access a component of the Fortinet Security Fabric?
Yes, Fortinet Zero Trust Network Access is natively integrated with the Fortinet Security Fabric. Which is allowing for consistent visibility and enforcement of policy across security solutions.
How can I deploy Fortinet ZTNA in my company?
You can deploy Zero Trust Network Access through an approved partner. Such as Juara IT Solutions, who offers deployment, support, and consulting services that fit your business needs.